Configuring SAML with Okta
Step 1: Create a new SAML app in Okta
- Log in to your Okta admin dashboard.
- Navigate to Applications and click Create App Integration.
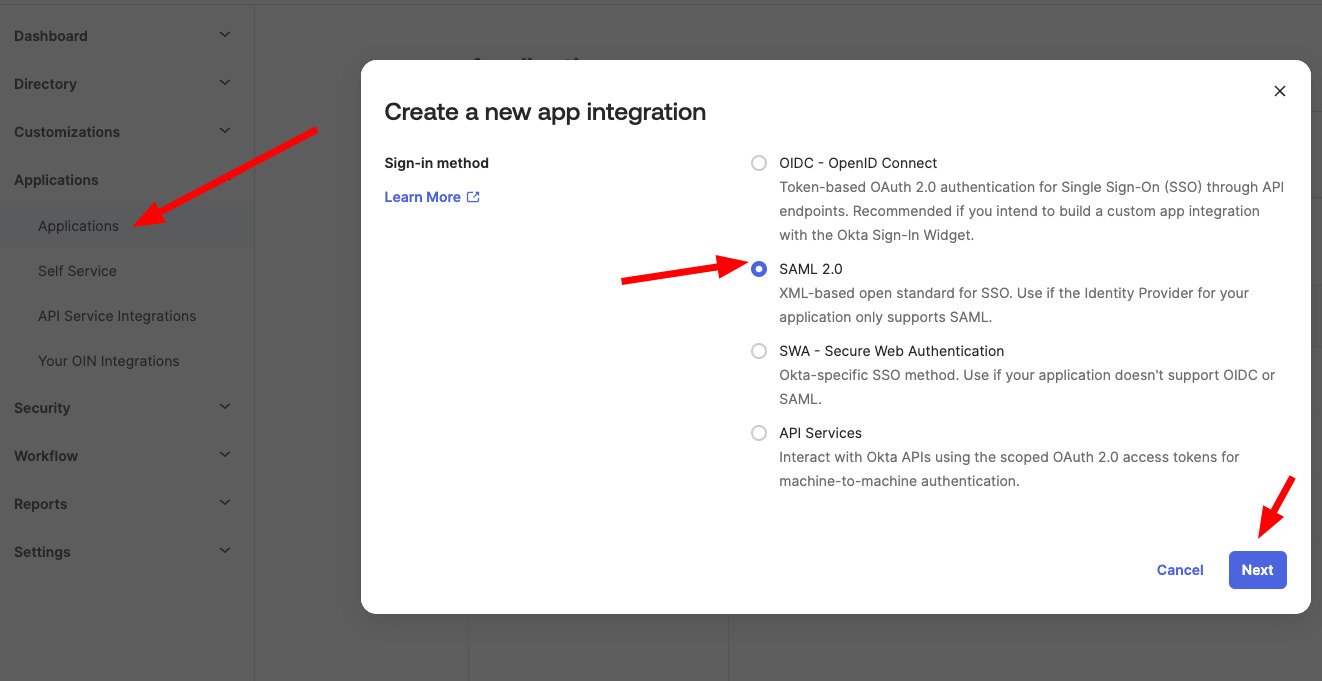
- Select SAML 2.0 as the sign-on method and click Next.
- Enter the App Name and optionally add a logo. Click Next.
Step 2: Configure SAML settings
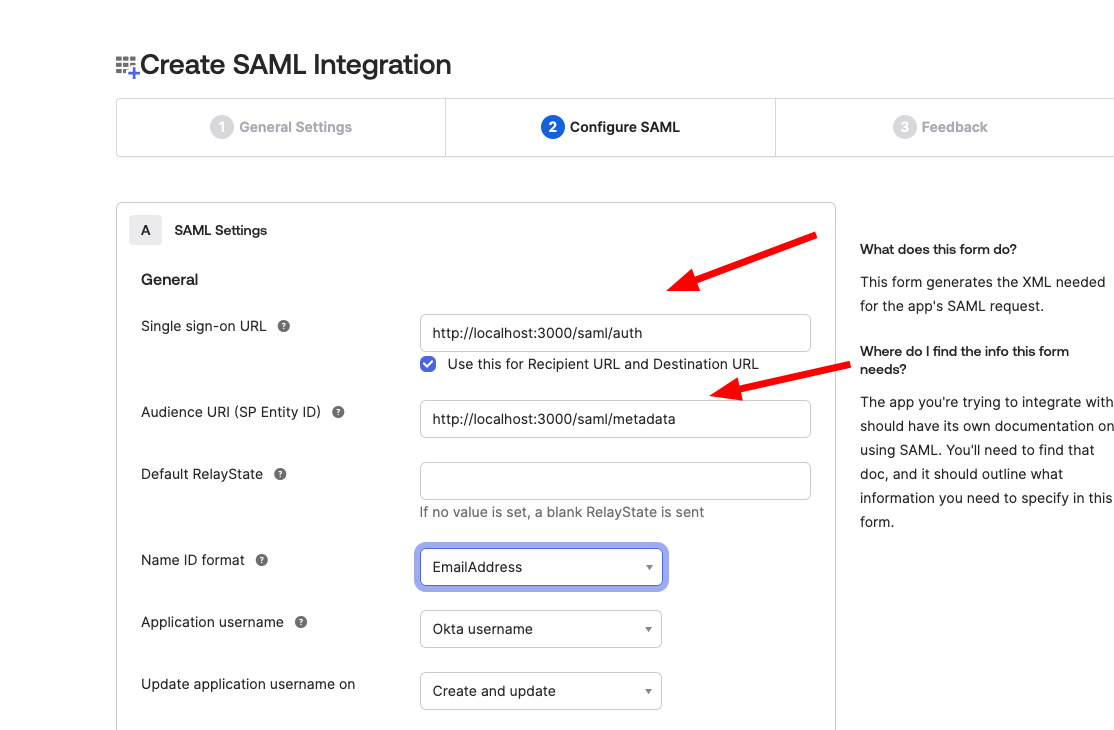
- In the General Settings, pass the SSO URL and Metadata URL from the DocuSeal application settings found on the DocuSeal SAML SSO page.
- SSO URL: Paste the SSO URL provided by DocuSeal.
- Entity ID: Use the Metadata URL from DocuSeal.
- Set the Name ID Format to EmailAddress and ensure that the Application username is also set to Email.
- Click Next to proceed to the feedback section.
Step 3: Application feedback
- Select I’m an Okta customer adding an internal app.
- Check the box This is an internal app that we have created.
- Click Finish.
Step 4: Retrieve Okta Sign-On URL
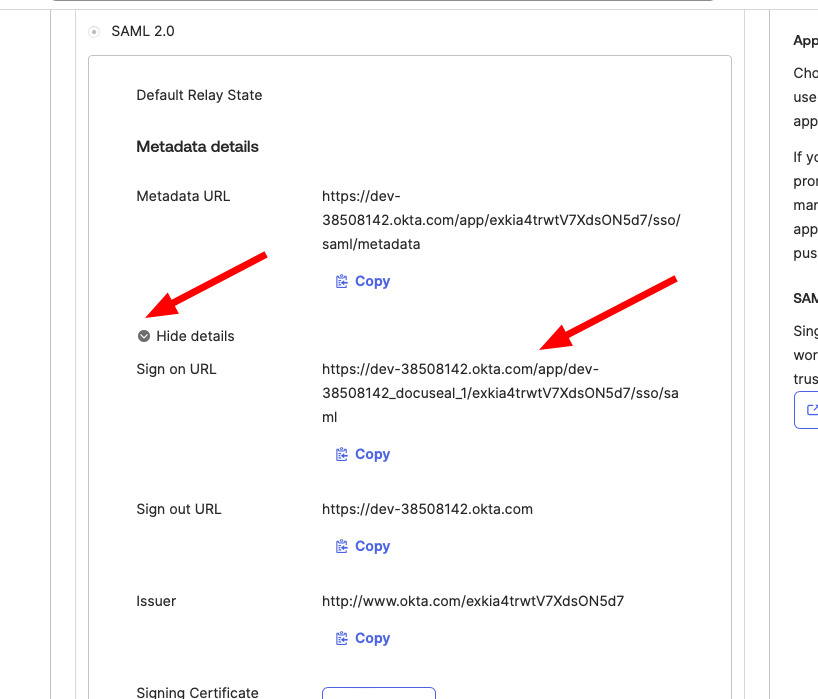
- Expand the Sign-On tab in the newly created SAML app settings.
- Copy the Okta Sign-On URL.
Step 5: Configure DocuSeal with Okta information
- In the DocuSeal SAML SSO page, paste the copied Sign-On URL to the SSO Service URL field.
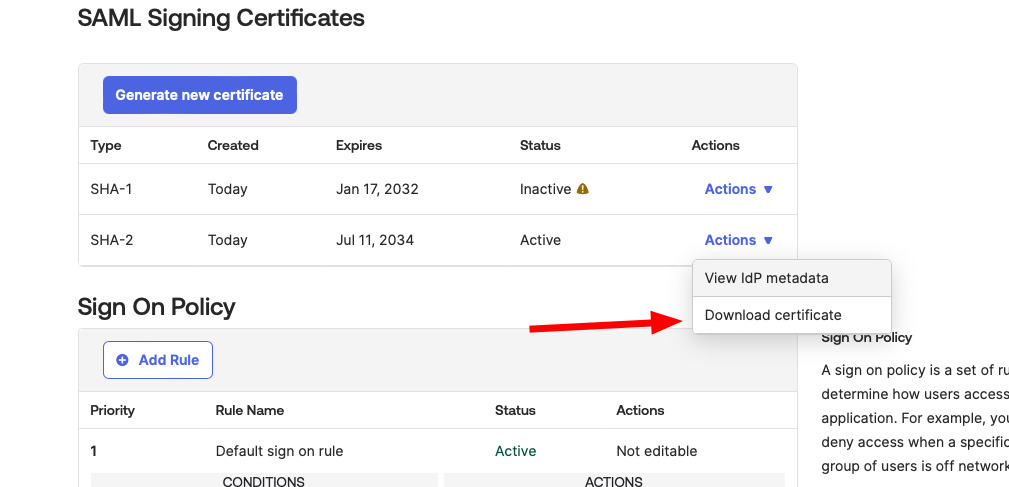
- Additionally, download the certificate from Okta:
- Go to the Sign-On tab and click on View Setup Instructions.
- Download the certificate in .pem format.
- Open the .pem file in a text editor and copy its contents.
- Paste the copied certificate content into the Certificate field in the DocuSeal SAML SSO page.
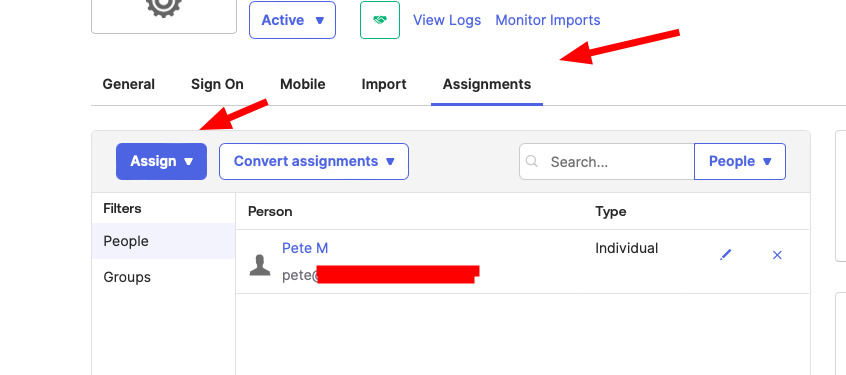
Step 6: Assign users to the SAML app
- Go back to the application settings in Okta.
- Navigate to the Assignments tab.
- Click Assign and choose Assign to People or Assign to Groups.
- Select the users or groups you want to assign to this SAML app.
Ensure that the email addresses of your users in DocuSeal match the assigned Okta user email addresses.
This is crucial for the SAML SSO to function correctly.
This is crucial for the SAML SSO to function correctly.